Install mod_remoteip in Apache2
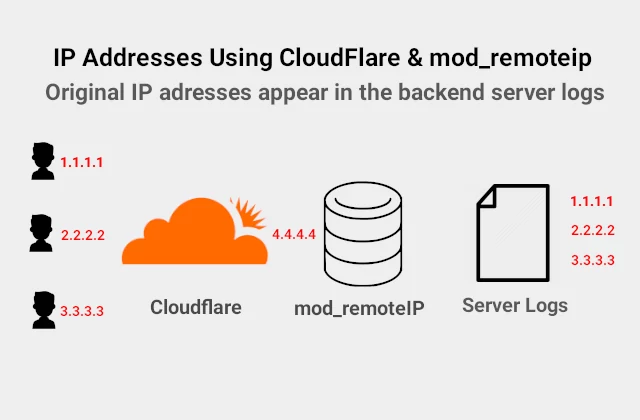
Install mod_remoteip Table of Contents Why using mod_remoteip in Apache2 How to get the real client IP Address from Cloudflare mod_remoteip mod_cloudflare How to Install mod_remoteip on Ubuntu Why Using mode_remoteip in Apache2 Mod_remoteip allows Apache2 to get the visitor IP from requests received from proxy servers and load balancers. It gives you the actual…